
Engaging, informative and effective, our training solutions help drive signigicant, sustainable culture change. Our content is create by instrauctional design professionals and backed by skilled cybersecurity experts. The results more awards than any other cybersecurity training firm.
-
About this course:
Learn everything you need to know about the GDPR with the award-winning online training team at Good e-Learning!The General Data Protection Regulation is shaping policies and practices not only in IT, but throughout virtually every department in organizations across the world. This course will explain the GDPR in simple terms, equipping you to make effective decisions and collaborate with GDPR compliance officers to ensure your business is toeing the line. Kickstart your GDPR training today!
-
What will you learn by taking this course?
The role of leaders and decision-makers in GDPR compliance
The purpose and contents of the GDPR
Everything required to engage in further discussions with GDPR specialists
-
Why should you take this course?
Good e-Learning is an award-winning online training provider
According to the UK Information Commissioner’s Office (ICO), step one to becoming GDPR-compliant is raising awareness in your organization
The GDPR applies to any organization or individual who processes data from within the European Union or European Economic Area
GDPR compliance is essential not only for avoiding significant fines (up to €20 million or 4% of an organization’s annual global turnover - whichever is larger), but also maintaining the confidence of clients and stakeholders
Good e-Learning courses feature a variety of online training assets, including instructor-led videos and customized graphics - each created with help from specialists
-
Module 1: Introduction
Learning Objectives
Welcome
The Data Protection Directive (DPD)
GDPR – Recognizing Advances in Technology
GDPR – Recognizing Advances in Consumer Rights -
Module 2: The Basics
Learning Objectives
Important Dates
The Scope -
Module 3: Personal Data
Learning Objectives
Personal Data
Special Categories of Data
Pseudonymized Data -
Module 4: The Roles
Learning Objectives
The Roles
Data Subject
Data Controller
Data Processor
Data Protection Officer (DPO) -
Module 5: GDPR Principles
Learning Objectives
GDPR Principles
Principle One: Processed Lawfully, Fairly and Transparently
Principle Two: Collected for Specified, Explicit and Legitimate Purposes
Principle Three: Adequate, Relevant and limited to what is Necessary for Processing
Principle Four: Accurate and Kept Up-to-datebr
Principle Five: Kept in a Form that Allows the Identification of Data Subjects only as Long as Necessary
Accountability -
Module 6: The Data Subject’s Rights
Learning Objectives
The Data Subject’s Rights
The Right to Information
The Right to Access
The Right to Rectification
The Right to Erasure
The Right to Restrict Processing -
Module 4: The Roles
Learning Objectives
The Legal Bases
Consent
Contractual Necessity
Vital Interest
Vital Interest
Legitimate Interest -
Module 8: Privacy Notices
Learning Objectives
Privacy Notice Rules under the GDPR
Privacy Notices - Why?
Privacy Notices - What?
Privacy Notices - Where?
Privacy Notices - When?
Privacy Notices - How?
-
What does 'GDPR' stand for?
'GDPR' stands for 'General Data Protection Regulation'.
-
What is the GDPR?
'GDPR' stands for the 'General Data Protection Regulation'. It is an EU regulation that addresses the transfer and storage of data in and outside the European Union and the European Economic Area.
-
Does the GDPR apply to every business?
The GDPR applies to any organization in or outside the EU that stores or transfers data from within the EU. It also applies to individuals, unless they utilize data solely for 'domestic or personal activity'.In short, any business from a self-employed trader to an international conglomerate can find GDPR applies to them.
-
What is the value of GDPR training?
With the GDPR applying to all organizations which utilize EU data, qualified data protection officers are in extremely high demand. According to Glassdoor, data protection officers in the UK can earn between £29,000 and over £89,000, while in the US they can earn up to $150,000 according to Medium.
-
What are the penalties for failing to be GDPR-compliant?
The fines for failing to be GDPR compliant depend on which articles are breached. The first choice is up to €10 million, or 2% annual global turnover, while the second is up to €20 million, or 4% annual global turnover. In both cases, the fee will be whichever option is higher.
-
Why is the GDPR so important?
The GDPR is important in two respects: firstly, it protects the data rights of EU citizens. Secondly, it clarifies exactly what steps organizations are required to take in order to safeguard these rights and minimize the possibility of data breaches.
-
How does the GDPR work?
The GDPR works by clarifying what organizations must do in order to protect customer data, setting strict standards for accountability and compliance. It also imposes harsh fines on businesses which fail to take the necessary steps.
-
Who can benefit from studying the GDPR?
The GDPR works by clarifying what organizations must do in order to protect customer data, setting strict standards for accountability and compliance. It also imposes harsh fines on businesses which fail to take the necessary steps.
-
What other frameworks can complement GDPR?
The GDPR is highly compatible with COBIT 2019, a framework dedicated to aligning business and IT goals. It can also be complemented by frameworks like ITIL 4, which prioritize compliance.
- Key Features:
- Created by a Security expert :
- Access period : 12 months
- Course duration : 1+ hours
- Quizzes & revision exams :
- Certificate of completion :
- Support :

What is Dark Web
Only 4% of the Internet is publicly accessible and index by normal search engines such as Google, Yahoo, or Bing. This is known as the Surface Web. The other 96% of the Internet, is made up of the Deep Web. Within the Deep Web are a subset of Dark Nets. It is the collection of these Dark Nets that make up the Dark Web.
The dark web is a part of the internet that isn't indexed by search engines. You've no doubt heard talk of the “dark web” as a hotbed of criminal activity — and it is. The dark web is a subset of the deep web that is intentionally hidden, requiring a specific browser—Tor—to access, as explained below. No one really knows the size of the dark web, but most estimates put it at around 5% of the total internet.
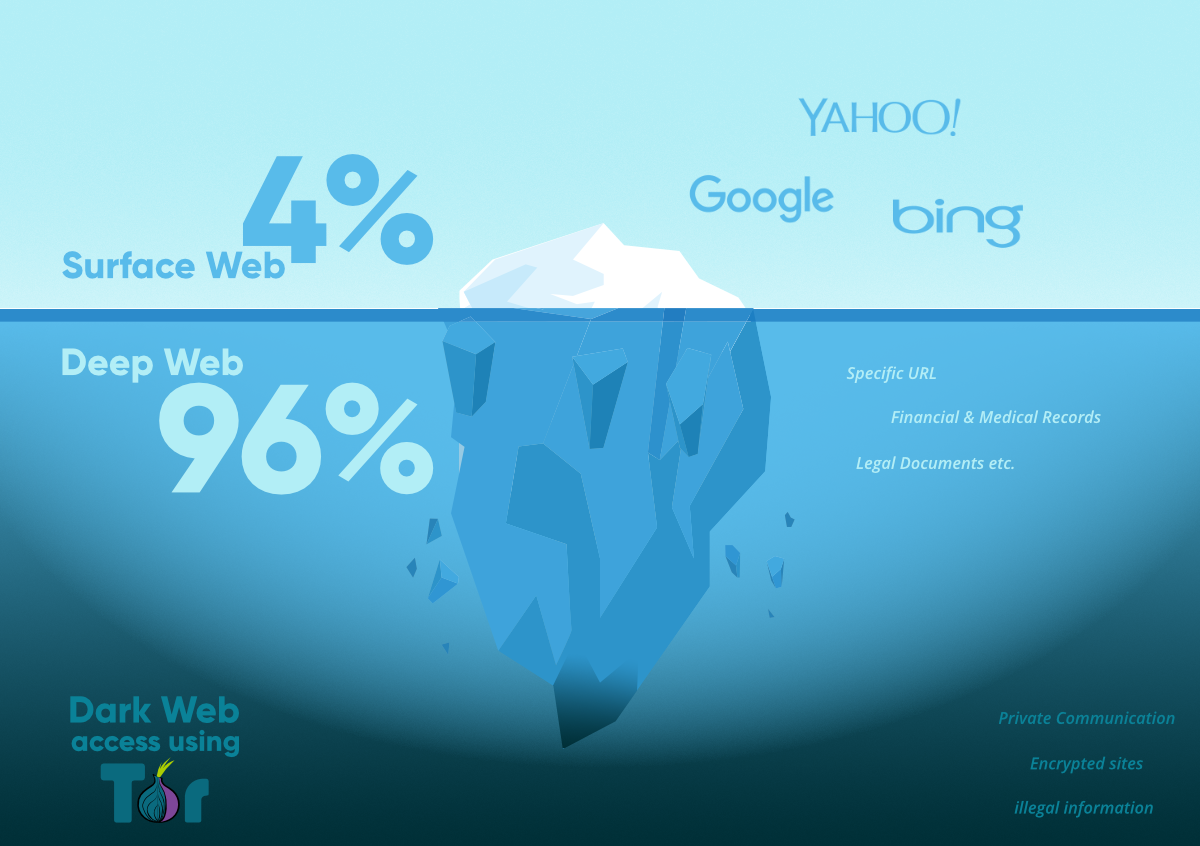
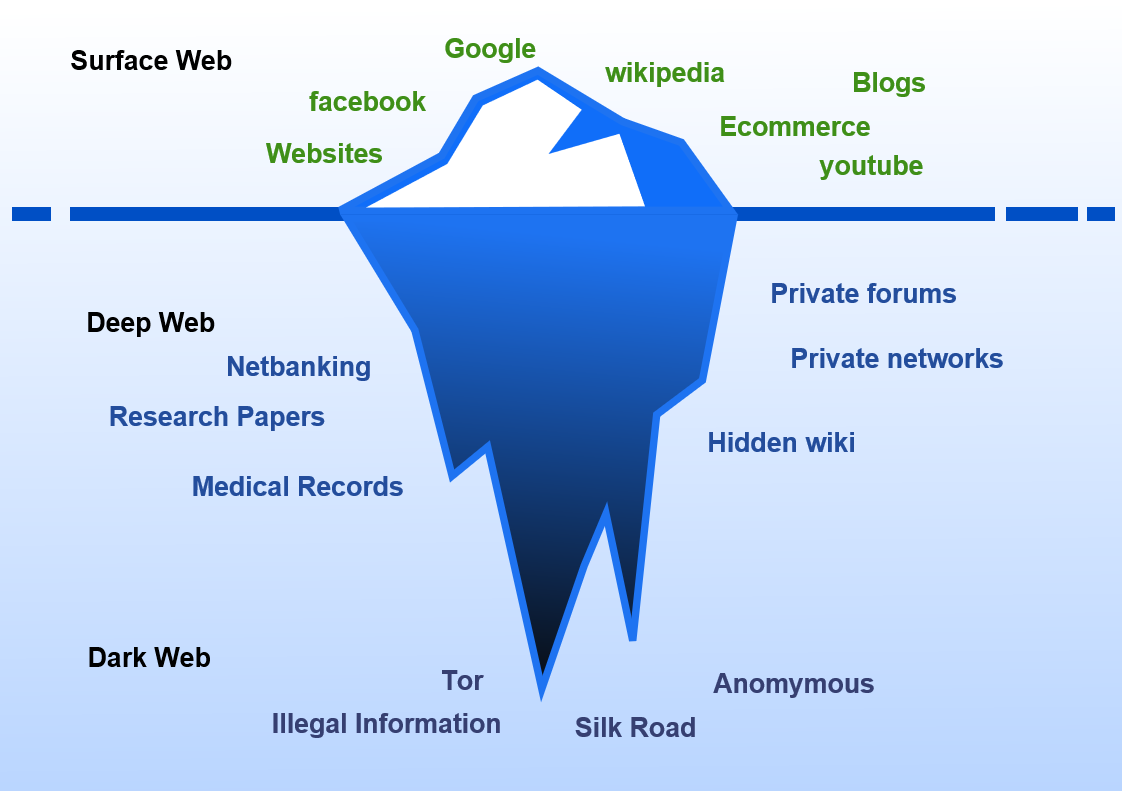
Comparison of Webs
| THE SURFACE WEB | THE DEEP WEB | THE DARK WEB | |
|---|---|---|---|
| How to Access | Traditional Search engine | Requerment password Encryption, or specially software | Requires Tor Project or simillar to view |
| Includes | All indexed web pages | All unindexed web pages | Subset of unindexed webpages inside the deep web |
| How to Access | Traditional Search engine | Requerment password Encryption, or specially software | Requires Tor Project or simillar to view |
| Includes | All indexed web pages | All unindexed web pages | Subset of unindexed webpages inside the deep web |
| How to Access | Traditional Search engine | Requerment password Encryption, or specially software | Requires Tor Project or simillar to view |
| Includes | All indexed web pages | All unindexed web pages | Subset of unindexed webpages inside the deep web |
Why do people use Dark Web
Why Dark Web Monitoring

Password Reuse
Compromised passwords increase the risk of external access to your clients' networks.

Social Engineering
Exposed personally identifiable information (PII) opens the door to convincing phishing attempts.

Internal Breach
With data breaches on the rise, unnoticed activity on the dark web puts organizations at risk.
How Will It Benefit Your Organization?
Businesses of any size can benefit from complete Dark Web Monitoring. But the right strategies must be put into place to fight all types of threats. With Dark Web Monitoring, you’ll have 24/7 surveillance to make sure that your company is 99% safe.

Effortless Rollout
Start monitoring in minutes
24 x 7 Monitoring from SOC
No software to deploy
Monitor in minutes

Proactive Protection
Bring the dark web to light
Real-time updates
Breached password data
Remediation ready to deploy

High Profit Margins
Increase your value and your margins
Easy add-on to your offering
Monitor domains, low-cost
Monthly payment terms
Real-Time Results, Instant Remediation
Dark Web Monitoring clients can get access to our training Program. With our security awareness training course, instantly educate users and lower the risk of a human-error induced data breach.


Priced for Partner, Profit Margins
As the threat landscape continues to grow, organizations cannot risk not knowing their dark web status. Providing around the 24 x 7 monitoring and protection for your organization should be priced to fit our MSP offering, allowing you to see high-profit margins and instant RIO.
Justify Additional Security With Real Data
Data breaches are scary and can be overwhelming for unprepared organizations, even when they aren't at fault. Circulate knowledge and security awareness to provide justification for remediation, proactive solutions, and additional security measures.

Why Aspire Tech
Award-winning courses
Aspire's award-winning online courses and programs are created and delivered by a renowned Cyber Security specialist.
The perfect fit for business
Plans for small to large businesses that are flexible to match your budget. There is a volume discount available.
Cost effective training
For a fraction of the expense of traditional classroom training, train thousands of employees in numerous locations.
Speak with an expert
Security awarness training curriculam
This course is your go-to resource for comprehebsive understanding of cyber security awareness training. It's core curriculam teaches your staff the fundamentals of security awarness best practices.

CORE Training
Our CORE security awareness training program trains employees on 12 critical security awareness topics quickly, economically and effectively. Lessons include:
- Intro to Security Awareness
- Computer Security
- Email Security
- Reporting Incidents
- Passwords
- Office Security
- Phishing
- Social Networking
- Web Security
- Public WiFi
- Mobile Security
- Information Protection

ADVANCED Training
Our ADVANCED security awareness training program addresses other security issues employees face with a follow-on curriculum:
- Social Engineering
- Data Loss Prevention (DLP)
- Safe Disposal
- Internet of Things
- Cloud Security
- Privacy
- Working Remotely
- Travel Security
- Insider Threat

ROLE-BASED Training
Our role-based security awareness training focuses on staff and entire organizations who handle sensitive data, have key responsibilities or positions that require unique knowledge:
- Security Awareness for IT Professionals
- Security Awareness for Managers
- Security Awareness for Executive
- Security Awareness for C-Level
- Security Awareness for Board

COMPLIANCE Training
Most organizations don’t have an effective way to distribute security policies and track that employees read and attest to follow them. Wouldn’t it be great to have a training that makes it easy for you to communicate, track, and report on compliance? We integrate policy tracking and compliance with training:
- PCI Compliance
- GDPR
- Data Protection
- HIPAA
Why Aspire Tech
Award-winning courses
Aspire's award-winning online course and programs are designed and taught by distinguished Cyber Security expert.
The perfect fit for any business
Plans for small to large organizations, with flexibility to fit inside your budget. Volume discounting available.
Cost effective training
Train thousands of staff members across multiple locations for a function of the cost of traditional classroom training.
Speak with an expert
Boost Engagement with delivering Communication Tools

Increase employee engagement with a different suite of communication tools like:
Posters
Promote your training program with visuals you can customize to brand... more
Newsletters
Send training updates and security best practice highlights directly... more
Digital wallpapers and web banners
Increase program engagement with colorful thought-provoking messaging... more
Training Videos/Animations
Strengthen key awareness concepts and skills through stylish visual... more
Why Aspire Tech
Award-winning courses
Aspire's award-winning online courses and programs are created and delivered by a renowned Cyber Security specialist.
The perfect fit for business
Plans for small to large businesses that are flexible to match your budget. There is a volume discount available.
Cost effective training
For a fraction of the expense of traditional classroom training, train thousands of employees in numerous locations.