
SECURITY AWARENESS TRAINING
Engage your employees to be the first line of defense
Giving out sensitive data to people without first authenticating their identity and access privileges is one of the most common and worst mistakes employees can make. Allowing a stranger inside an organization without authorization is yet another example of a broken link in the human firewall chain.
-
About this course
The businesses are always in danger of threats from within the organization. An organization's security can be easily crushed by an employee or human error, where careless or ignorant staffs are the second assuredly cause of a serious security breach
-
Why this course is important ?
Within recent years, data breaches resulting from phishing attacks have increased substantially and are perhaps one of the most dangerous threats to commercial, governmental, and nonprofit organizations today. As phishing attacks evolve by becoming more customized and sophisticated, these organizations must develop strategies to not only train their members to detect and avoid these attacks on an individual basis but also better coordinate and motivate members to work together to combat these attacks. By building this “human firewall”, individuals are included as part of the solution when managing information technology security, rather than the problem where they are frequently considered the “weakest link”.
-
Why should you take this course?
Building the Human Firewall to Combat Socially Engineered Attacks training course helps organizations to maintain constant vigilance and be aware of threats to our organization. Building the Human Firewall: Organization-Wide Strategies to Combat Socially Engineered Attacks. The definition of a human firewall is fairly straightforward. It is essentially a commitment of a group of employees to follow best practices to prevent as well as report any data breaches or suspicious activity. The more employees you have committed to being a part of the firewall, the stronger it gets.
-
Chapter 1: Information Security Protection
-
Chapter 2: Safe Internet Browsing
-
Chapter 3: Social Engineering
-
Chapter 4: The 5 Traits of a Human firewall
✔️ Thinking before clicking
✔️ Respecting privileged access
✔️ Always the following policy
✔️ Using situational awareness
✔️ Reporting incidents immediately
-
Chapter 5: Six Tools Every Human Firewall Has In Their Security Awareness Utility Belt
✔️ Password Manager
✔️ A 2-3-4 Backup System
✔️ Authenticator Apps
✔️ VPN
✔️ Antivirus Software
✔️ Ad Blockers
-
What are 3 key ingredients for an excellent human firewall?
Three Key Elements for Building an Effective Human Firewall
✔️ Make People Care about Cybersecurity. A key element of building an effective human firewall is to make employees care about cybersecurity.
✔️ Build Awareness and Knowledge.
✔️ Measure and Monitor.
-
What does human firewall mean?
The definition of a human firewall is fairly straightforward. It is essentially a commitment of a group of employees to follow best practices to prevent as well as report any data breaches or suspicious activity. The more employees you have committed to being a part of the firewall, the stronger it gets.
-
What is an example of a human firewall?
Giving out sensitive data to people without first authenticating their identity and access privileges is one of the most common and worst mistakes employees can make. Allowing a stranger inside an organization without authorization is yet another example of a broken link in the human firewall chain.
-
Why do I need to worry about information security?
The threats are real – and it’s not some shady character with a gray hooded sweatshirt looking at scrolling lines of green code. From a volume standpoint, it’s largely automated and in a general broadcast to large swaths of the Internet (although the most significant threats are targeted). Cisco Talos has hard statistics on the fact that roughly 85% of all email traversing the Internet is spam – either marketing or malware. The spam filters do a good job at catching and stopping that 85% but some are bound to go unnoticed and pass through to your users.
- Key Features:
- Created by a Security expert :
- Access period : 12 months
- Course duration : 40+ hours
- Quizzes & revision exams :
- Certificate of completion :
- Support : 24/7 hours
Data breaches, viruses, and other malware via phishing and social engineering
For many years, data breaches, viruses, and other malware spread by phishing and social engineering have made security headlines, with phishing being one of the most prevalent social threat vectors for any business.





Cyber security awareness training for employees is a must for successful data security protection. Aspire created an information security awareness program that is simple to follow and does not interfere with employees' normal tasks. Your staff will have an easy-to-use platform thanks to our phishing simulation software and security awareness training.
Employees are not a security problem. They are part of the solution
Aspire’s advanced interactive tests and web-based security awareness training program trains employees on 21 critical security awareness topics quickly, economically, and effectively.

95% of cyber security breaches are caused by human error.
IBM Cyber Security Intelligence Index

9 out of 10 US businesses fall victim to cyber security incidents each year.
HSB Survey

$4M is the total cost of the average cyber security breach.
Ponemon Institute
Engaging security awareness training

Aspire’s interactive tests and web-based trainings can be used to determine the users’ level of knowledge about security. Educate employees and motivate behavior change with personalized security awareness and training.
Cloud-based and integrated with our Security Awareness Training, our service is easily deployed either as self-managed or managed service. Meet and document compliance, build awareness with engaging campaigns or deliver training automatically to employees who need it most.
Dedicated training portal
With our security awareness training platform each of your employees will have access to their own portal to take online courses at any time.
This minimizes disruptions to employee productivity.
The training portal is mobile-friendly, allowing users to take training on any device from anywhere.
This portal will help the employees to develop their Cyber Security knowledge. They will aware of different Cyber Attacks like phishing, malware, etc., and will gather knowledge of preventing these attacks. Our portal has covered every topic in Cyber Security awareness. That will be the most beneficial part for employees. As our portal is user-friendly, an employee can easily access it from any device.
Real-time reporting

Measure your organization’s compliance score, phish rate and more to share progress with stakeholders and prove success.
Training is only useful if it is finished within a reasonable amount of time. Management can readily assess the status of staff training thanks to real-time data.
The reports give real-time data so that workers who need to finish training may be reminded.
One of the reasons why incorporating real-time data into cyber security makes so much sense is because security specialists are struggling to keep up with the dangers they confront. They fail to notice them within the periods established by CrowdStrike as recommended practices for cyber security professionals.
Customize / Create new courses
Our website is adaptable. Do you need to teach your staff on other topics because your company requires it? Create your own courses or alter current ones using the platform. Fill up the blanks with your own questions and answers.
Create training materials quickly and easily, then distribute them to staff. Use a combination of standard and customized training to meet the needs of your staff and company.
We are constantly concerned about the well-being of our staff. Protect your company against malware, ransomware, phishing, and social engineering by taking this cyber security awareness course. Protect your data and networks, as well as prevent unwanted people from accessing them.
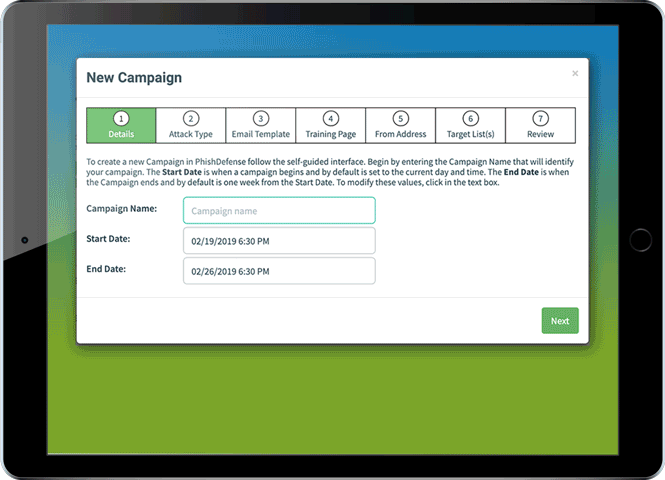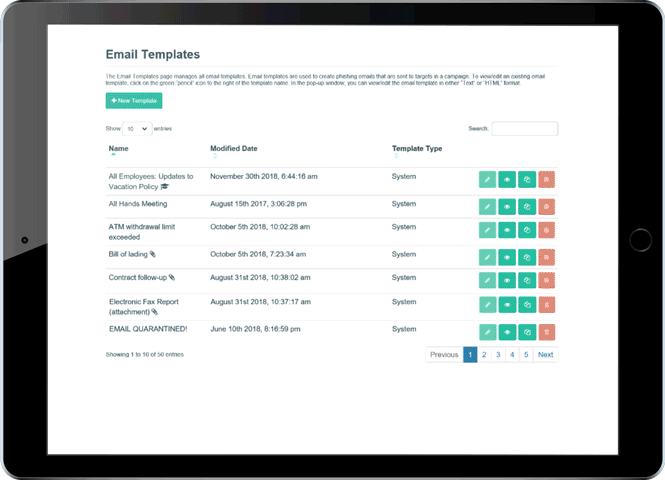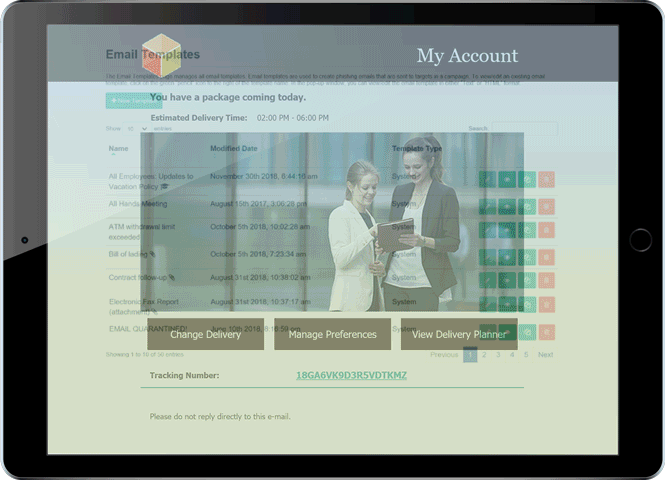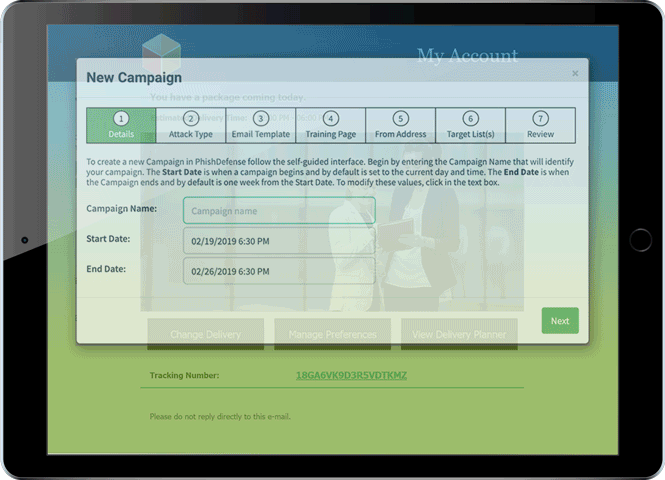
Repeat testing & continuing education
According to Verizon, phishing emails are the source of 67% of all cyber intrusions. You can defend against email-based social engineering assaults and reinforce your most overlooked security asset by using our Phishing Simulation tools. Your staff is on the front lines of the anti-phishing fight, and without them, you can't win. To produce a workforce that is immune to hacker traps, Aspire highly advises a mix of simulated phishing assaults and tailored training.
Enterprises must develop a rigorous strategy to security testing for their applications, websites, and any other digital product capable of receiving or keeping crucial data from consumers, clients, and partners today more than ever before. Furthermore, businesses must take proactive steps to preserve their brand image on social media, as buyers increasingly use these platforms to research products before making purchases
Security awarness training curriculam
This course is your go-to resource for comprehebsive understanding of cyber security awareness training. It's core curriculam teaches your staff the fundamentals of security awarness best practices.

CORE Training
Our core security awareness training program trains employees on 12 critical security awareness topics quickly, economically and effectively. Lessons include:
- Intro to Security Awareness
- Computer Security
- Email Security
- Reporting Incidents
- Passwords
- Office Security
- Phishing
- Social Networking
- Web Security
- Public WiFi
- Mobile Security
- Information Protection

ADVANCED Training
Our advanced security awareness training program addresses other security issues employees face with a follow-on curriculum:
- Social Engineering
- Data Loss Prevention (DLP)
- Safe Disposal
- Internet of Things
- Cloud Security
- Privacy
- Working Remotely
- Travel Security
- Insider Threat

ROLE-BASED Training
Our role-based security awareness training focuses on staff and entire organizations who handle sensitive data, that require unique:
- Security Awareness for Managers
- Security Awareness for Executive
- Security Awareness for C-Level
- Security Awareness for Board
- Security Awareness for IT Professionals

COMPLIANCE Training
Most organizations don’t have an effective way to distribute security policies and track that employees read and attest to follow them.
- PCI Compliance
- GDPR
- Data Protection
- HIPAA
Boost Engagement with delivering Communication Tools

Increase employee engagement with a different suite of communication tools like:
Posters
Promote your training program with visuals you can customize to brand... more
Newsletters
Send training updates and security best practice highlights directly... more
Digital wallpapers and web banners
Increase program engagement with colorful thought-provoking messaging... more
Training Videos/Animations
Strengthen key awareness concepts and skills through stylish visual... more
Why Aspire Tech
Award-winning courses
Aspire's award-winning online courses and programs are created and delivered by a renowned Cyber Security specialist.
The perfect fit for business
Plans for small to large businesses that are flexible to match your budget. There is a volume discount available.
Cost effective training
For a fraction of the expense of traditional classroom training, train thousands of employees in numerous locations.