
Phishing awareness training educates employees on how to spot and report suspected phishing attempts, to protect themselves and the company from cybercriminals, hackers, and other bad actors who want to disrupt and steal from your organization.
-
About this course
The best way to combat phishing is through information security awareness training. People need to be educated about how not to be fooled. Everyone in the workforce needs to be aware of the kinds of tricks fraudsters use and how to spot suspicious emails, attachments, links, or phone calls. All it takes is one person to make one wrong click. and there’s a data breach! The more people who are cautious and wise, the lower the risk.
-
Importance of Anti-Phishing Training
A phishing campaign is an email scam designed to steal personal information from victims. Cybercriminals use phishing, the fraudulent attempt to obtain sensitive information such as credit card details and login credentials, by disguising as a trustworthy organization or reputable person in email communication.
Phishing is a type of social engineering attack often used to steal user data, including login credentials and credit card numbers. It occurs when an attacker, masquerading as a trusted entity, dupes a victim into opening an email, instant message, or text message
-
Why should you take this course?
A test provides data on which employees have been baited by the phishing email by clicking on the corresponding links. Your users can learn to identify suspicious emails, and in turn, apply security awareness best practices, by having the chance to experience a phishing attack.
-
Chapter 1: Introduction of Phishing
-
Chapter 2: Common Types of Cybersecurity Attacks
-
Chapter 3: How Does Phishing Works
-
Chapter 4: Types of Phishing Attacks
✔️ Pharming ✔️ Spear Phishing ✔️ Whaling Phishing ✔️ Vishing ✔️ Smishing ✔️ Suspicious Link ✔️ Content Injection ✔️ Clone Phishing ✔️ Link Spoofing ✔️ Website Spoofing ✔️ Malicious and Covert Redirects ✔️ CEO Fraud ✔️ Deceptive Phishing ✔️ Business Domain Impersonation ✔️ Name Impersonation ✔️ Brand Impersonation ✔️ Search engine phishing -
Chapter 5: Causes of Phishing
-
Chapter 6: Effects of Phishing
-
Chapter 7: Necessary Safeguards Against Phishing Emails
-
Chapter 8: Monitor Results and Improve
-
Chapter 9: How Aspire Phishing tool can help in you
-
What is phishing?
Phishing is a common type of scam used to elicit confidential, lucrative, and/or sensitive information. Most often, phishing comes in the form of emails appearing to be sent from a trustworthy company or person but containing malicious links, requests for information, or harmful attachments. Some links in phishing emails contain malware which, if clicked, will install malware onto your device that can monitor your computer’s keyboard. These recordings capture information such as passwords or credit card numbers and then relay that data to identity thieves.
-
What kind of information should I protect?
You should protect all sensitive and confidential data. For information on what is considered sensitive and confidential data
-
What is the difference between spam and phishing?
Spam is electronic junk mail or, more broadly, unsolicited sales emails. Spam differs from phishing because spam emails will not request sensitive or confidential information; rather they will attempt to sell you an item, service, or subscription.
-
Is phishing done only through email?
No, scammers also utilize phone calls, SMS texts, and social media sites to trick you into giving up sensitive and confidential information.
-
Are we prepared to respond to a cyber-attack?
It’s important that you have the expertise, skillset, and knowledge that’s required to manage an incident end to end. There are cross-functional skills that are needed. Move away from incident response and into incident management. Preparation is imperative, which requires time, dollars, and people.
-
How are we able to detect a cyber-attack?
It’s important to keep in mind there isn’t one, a single tool for this. And there’s no such thing as 100% protected. You need to determine which systems you are utilizing and how they integrate and interact with each other. Do they have the capability to aggregate data across systems to get a better understanding?
- Key Features:
- Created by a Security expert :
- Access period : 12 months
- Course duration : 40+ hours
- Quizzes & revision exams :
- Certificate of completion :
- Support : 24/7 hours
How Phishing Simulation Works
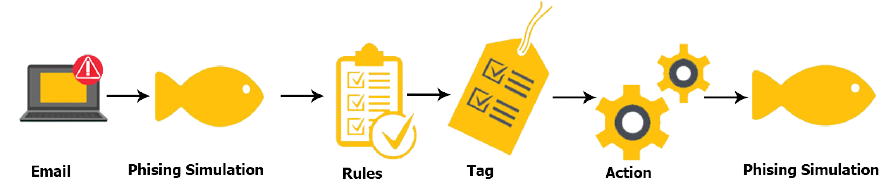
Phishing attacks can be one of the most dangerous cyber threats facing any organizations. With ever increasing numbers and sophistication of attacks, the danger is also increasing every day. Even the most sophisticated cyber security software and hardware isn’t able to identify and block all phishing attacks, preventing them from reaching your employees. Aspire phishing simulation tool processes user-reported phishing and other suspicious emails by grouping and categorizing emails based on rules, tags, and actions.
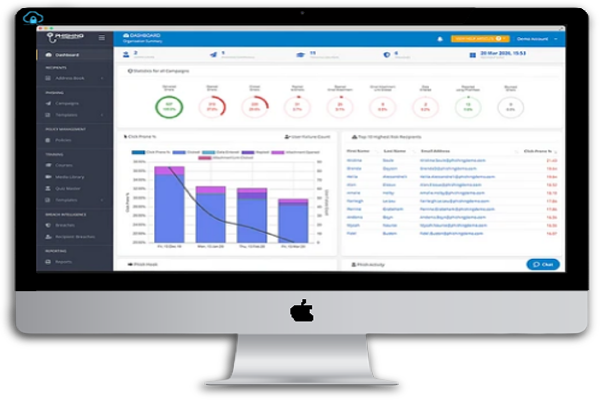
Employee cyber security awareness training is a key requirement for an effective information security protection. Aspire developed an information security awareness curriculum that is easy-to-understand and does not affect with employee’s daily activities. Through our phishing simulation software and our security awareness training, your organizations will have an easy-to-use platform for employees.
Phishing Simulations, Testing & Training
Aspire's managed phishing service, a team of experts is working on creating and running phishing simulation tests and cybersecurity training courses. Notify employees using phishing templates and training tools, or create your own templates to prepare your employees for company threats. Some employees may need a more personalized attack vector, such as B. Use of job title or department.
As technology advances, cybercriminals are adapting phishing attacks to make it harder for machines and people to identify malicious messages. Traditional phishing emails target hundreds or thousands of recipients at the same time. These are designed to trick users into clicking on URLs to web pages that ask for personal information. Spear phishing emails are targeted and personal. Attackers pretend to know the victim by pretending to be a trusted source, ensuring that an unsuspecting user trusts the victim when they request sensitive information. Both types of attacks have important indicators that users can be aware of to determine if an email is genuine or fraudulent.
Assess Vulnerability & Train Employees

As the campaign runs, our phishing service tracks each and every phishing message so you can quickly identify vulnerable users and immediately:
- Alert them to their mistake and the potential danger
- Redirect at-risk users to a targeted training session
- Show how they could have identified the phishing attack
For those organizations that prefer not to let employees know they were phished, that is an option too.
Launch Phishing Campaigns and Training to Those Employees Who Need it the Most
It's time to start planning your campaign. Give the campaign a name and a description, choose start and end dates, choose your email message and landing page templates, and then decide on your target demographic (s).
It's that simple and quick. Campaign execution is automatic once you start a phishing program, and you can check the results on the phishing dashboard right away. You have complete control over when and how campaigns are launched.
Simulated phishing efforts, such as mass phishing, spear phishing, and whaling, reinforce staff training, help you understand your own risk, and enhance workforce resiliency.

Organizational Resistance
Phishing simulation should be done regularly and often.Aspire phishing simulation service allows you to develop targeted phishing campaigns, schedule and test repeatedly. Its powerful Dashboard enables you quickly track how your campaigns are doing and assess whether you are reducing your organizational risk by building user resistance.
Organizational inertia is the tendency for an organization as a whole to resist change and want to maintain the status quo. Companies that suffer from inertia become inflexible and can’t adapt to environmental or internal demands for change. Some of the signs that organizational inertia is in play are through internal power struggles, poor decision-making processes and bureaucratic organizational structures.
Organizational cultures and reward systems can foster resistance or acceptance of change. A culture that promotes high levels of trust and cooperation lays the foundation for employees and their acceptance and instigation of change. If employees are punished for honest mistakes, if new ideas aren’t rewarded, and managers aren’t prepared for daily issues with proper training, then that organization is ripe for change resistance.
Easily Deploy & Simulate Phishing Attacks
Aspire’s phishing simulation tools enables you to automatically send simulated phishing attacks to your employees, identify vulnerable employees, and provide real-time training.
Cloud-based and integrated with our Security Awareness Training, our service is easily deployed either as self-managed or managed service.
As you conduct your phishing awareness training, you are adding value to your overall security awareness initiative. By testing the knowledge and skills of your employees, you are contributing to behavior change at larger, whereby users are encouraged to train and become more informed and alert in matters of cyber security.

Detailed Reporting
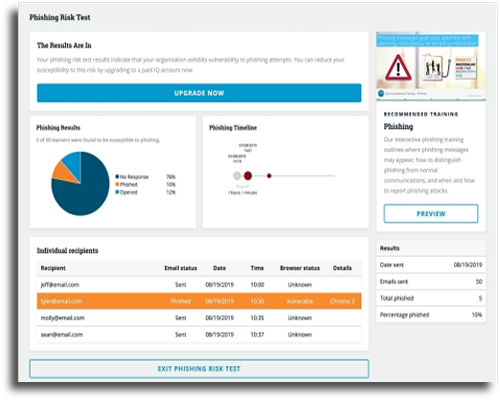
With our security awareness training platform each of your employees will have access to their own portal to take online courses at any times.
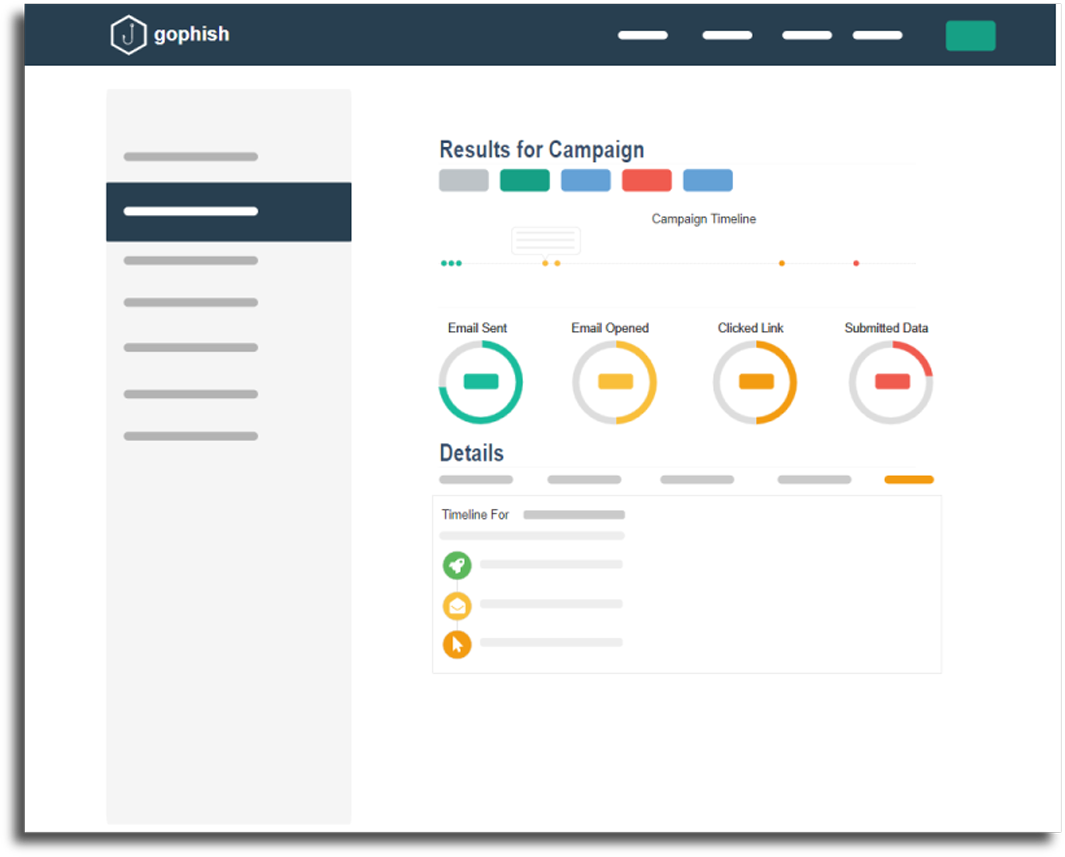
The reporting dashboard provides an in-depth analysis of specific phishing campaigns. Organizations can easily identify the percentage of users that are vulnerable to attack, which device they accessed the phishing email from, and the metrics can be broken down further to evaluate specific departments and user groups.
The reports will focus if your awareness campaign is making progress and outline the need for any additional employees training.
Phishing training curriculum
This course is your go-to resource for comprehensive understanding of cyber security awareness training. It's core curriculam teaches your staff the fundamentals of security awareness best practices.

CORE Training
Our CORE security awareness training program trains employees on 12 critical security awareness topics quickly, economically and effectively. Lessons include:
- Intro to Security Awareness
- Computer Security
- Email Security
- Reporting Incidents
- Passwords
- Office Security
- Phishing
- Social Networking
- Web Security
- Public WiFi
- Mobile Security
- Information Protection

ADVANCED Training
Our ADVANCED security awareness training program addresses other security issues employees face with a follow-on curriculum:
- Social Engineering
- Data Loss Prevention (DLP)
- Safe Disposal
- Internet of Things
- Cloud Security
- Privacy
- Working Remotely
- Travel Security
- Insider Threat

ROLE-BASED Training
Our role-based security awareness training focuses on staff and entire organizations who handle sensitive data, have key responsibilities or positions that require unique knowledge:
- Security Awareness for IT Professionals
- Security Awareness for Managers
- Security Awareness for Executive
- Security Awareness for C-Level
- Security Awareness for Board

COMPLIANCE Training
Most organizations don’t have an effective way to distribute security policies and track that employees read and attest to follow them. Wouldn’t it be great to have a training that makes it easy for you to communicate, track, and report on compliance? We integrate policy tracking and compliance with training:
- PCI Compliance
- GDPR
- Data Protection
- HIPAA
Boost Engagement with delivering Communication Tools

Increase employee engagement with a different suite of communication tools like:
Posters
Promote your training program with visuals you can customize to brand... more
Newsletters
Send training updates and security best practice highlights directly... more
Digital wallpapers and web banners
Increase program engagement with colorful thought-provoking messaging... more
Training Videos/Animations
Strengthen key awareness concepts and skills through stylish visual... more
Why Aspire Tech
Award-winning courses
Aspire's award-winning online courses and programs are created and delivered by a renowned Cyber Security specialist.
The perfect fit for business
Plans for small to large businesses that are flexible to match your budget. There is a volume discount available.
Cost effective training
For a fraction of the expense of traditional classroom training, train thousands of employees in numerous locations.